Data rooms have become essential for secure document exchange and collaboration, especially when sensitive information like PII is involved. Their popularity is fueled by the need for companies to protect confidential data during transactions, fundraising, audits, and research projects. Data rooms are essential for securely managing and sharing sensitive information in a variety of scenarios:
Agency Collaboration: Agencies can securely share sensitive client data and collaborate on projects while maintaining confidentiality.
Brand Partnerships and Joint Ventures: Collaborate on marketing campaigns and joint ventures while protecting sensitive information.
E-commerce and Payment Processing Development: Protect sensitive data like customer payment information and transaction records during development.
Influencer Marketing Campaigns: Securely manage influencer agreements and campaign materials and track activities.
Mergers and Acquisitions (M&A) Due Diligence: Data rooms provide a secure platform for sharing confidential documents with potential investors or buyers during the M&A process.
Public Relations (PR) Crisis Management: Data rooms centralize critical information for PR teams to effectively manage crises.
Software or Database Development: Securely share code, documentation, and sensitive data with development teams and partners throughout the software development lifecycle.
Working with Subcontractors: Securely access project plans, specifications, and other sensitive documents while maintaining control over confidential information.
Data rooms provide a secure and controlled environment for sharing and managing sensitive documents with internal and external stakeholders, reducing the risks of data breaches and ensuring compliance with privacy regulations.
Tresorit
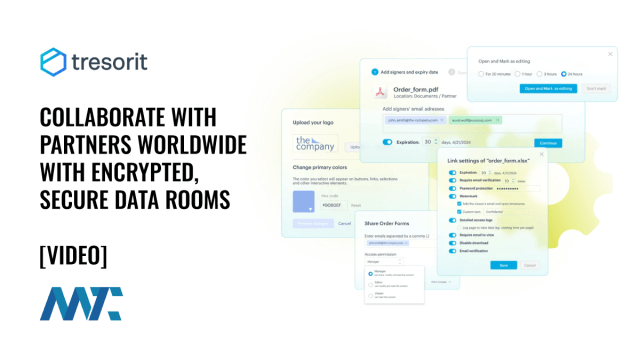
Tresorit is a cloud-based file-sharing and collaboration platform that prioritizes security and compliance. With its end-to-end encrypted data rooms, Tresorit ensures that sensitive data remains confidential and protected from unauthorized access.
Unlike traditional file-sharing services, Tresorit encrypts files on the user’s device before uploading them to the cloud. This means that even Tresorit employees cannot access the content of your files. This zero-knowledge approach to security is critical for businesses dealing with sensitive data, ensuring that only authorized individuals can access and view the information.
Tresorit Feature List
Tresorit data rooms offer a comprehensive suite of features to enhance security, streamline collaboration, and ensure compliance. With end-to-end encryption, granular access controls, and detailed audit trails, Tresorit empowers businesses to protect their sensitive information and control their data.
Activity Logs and Audit Trails: Maintain comprehensive records of all user activity within the data room to ensure compliance with regulatory requirements and internal security policies.
Comply with Industry Standards: Meet the stringent requirements of industry-specific regulations, including CCPA, CJIS, DORA, FINRA, GDPR, HIPAA, ITAR, NIS2, and TISAX.
Get Agreements signed: Expedite contract approvals and agreements with legally binding e-signatures, ensuring document authenticity and integrity.
Logs and Audit Trails: Track all data room activities with detailed audit trails, providing an extra layer of security and accountability.
Maintain full control over external users and content: Grant or revoke access to specific files or folders for internal and external users, ensuring that sensitive information is only accessible to authorized individuals.
White-labeling: Customize the data room with your company’s branding to maintain a consistent corporate identity and enhance professional interactions.
Work from anywhere: Access and collaborate on documents from any device, anytime, anywhere, with Tresorit’s web, desktop, and mobile applications.
Getting Started With Tresorit
Getting started with Tresorit is simple. Sign up for an account, create a data room, and invite your collaborators. Tresorit’s intuitive interface makes it easy to manage permissions, track activity, and ensure the secure exchange of sensitive information.
We’ve compared Tresorit to similar products on the market and we’ve concluded that it was covering our security requirements most efficiently.
Ivan Vladikin, CISO at AMATAS
Ready to experience peace of mind with Tresorit’s secure data rooms?
©2024 DK New Media, LLC, All rights reserved | Disclosure
Originally Published on Martech Zone: Tresorit: Securely Collaborate with Partners Worldwide with Encrypted Data Rooms